Researchers have discovered multiple Android apps, some that were available in Google Play after passing the company’s security vetting, that surreptitiously uploaded sensitive user information to spies working for the North Korean government.
Samples of the malware—named KoSpy by Lookout, the security firm that discovered it—masquerade as utility apps for managing files, app or OS updates, and device security. Behind the interfaces, the apps can collect a variety of information including SMS messages, call logs, location, files, nearby audio, and screenshots and send them to servers controlled by North Korean intelligence personnel. The apps target English language and Korean language speakers and have been available in at least two Android app marketplaces, including Google Play.
Think twice before installing
The surveillanceware masquerades as the following five different apps:
- 휴대폰 관리자 (Phone Manager)
- File Manager
- 스마트 관리자 (Smart Manager)
- 카카오 보안 (Kakao Security) and
- Software Update Utility
Besides Play, the apps have also been available in the third-party Apkpure market. The following image shows how one such app appeared in Play.
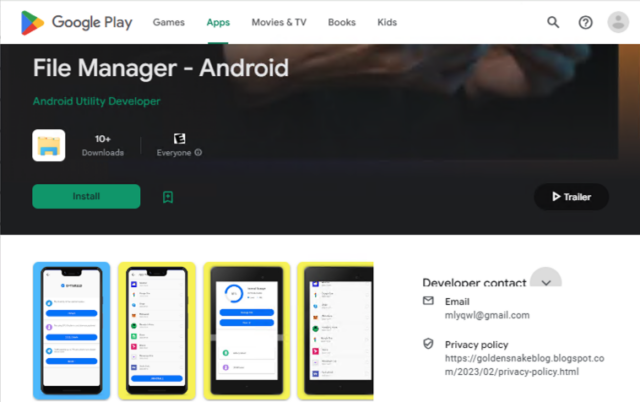
The image shows that the developer email address was mlyqwl@gmail[.]com and the privacy policy page for the app was located at https://goldensnakeblog.blogspot[.]com/2023/02/privacy-policy.html.
“I value your trust in providing us your Personal Information, thus we are striving to use commercially acceptable means of protecting it,” the page states. “But remember that no method of transmission over the internet, or method of electronic storage is 100% secure and reliable, and I cannot guarantee its absolute security.”
The page, which remained available at the time this post went live on Ars, has no reports of malice on Virus Total. By contrast, IP addresses hosting the command-and-control servers have previously hosted at least three domains that have been known since at least 2019 to host infrastructure used in North Korean spy operations.

